Applications and services of the Internet
Published:
Author: Yusuf Brima
Introduction
The Internet plays quite an invaluable role in this knowledge age since it is the cornerstone of every day-to-day information acquisition and sharing means. The Internet plays a pivotal role ranging from publishing Personal Home Pages to WhatsApping. The Internet provides an array of services that are exposed at the application layer which are user-supported. Hyper Text Transfer Protocol (HTTP) is the service that is generating the highest traffic over the Internet because of its apparent ease of use and general acceptance among users. HTTP provides web contents (hypermedia i.e., texts, graphics, audio and video) in the form of WebPages which are authored by designers. The WWW has, not surprisingly, been the most colossal library (digital) for knowledge in the history of civilization. Different technologies have phased the Web into different generations, with HTML (Hyper Text Markup Language) the underpinning technology for its thriving success.
 Services of the Internet
Services of the Internet
File Transfer, Access and Management (FTAM) is another service available over the Net; this provides directory and file access. File Transfer Protocol (FTP) is the underlying protocol for this service. FTP exploits the Internet to provide normal File System Management routines over the Internet (i.e., copy, cut, delete, paste and other operations) between End Systems over the Internet. FTP is used to transfer large contents between nodes over the Internet; a classic illustration is a transfer of a database from a workstation to a remote database server for hosting purpose and/ or collaboration among developers. FTP comes in has many implementations namely: TFTP (Trivial FTP), this performs only simple operations, with no authentication and is rarely used in interactive environments (Wikipedia, 2014). It is generally used for automated transfer of configuration or boot files between machines in a local environment (Wikipedia, 2014). SFTP (Secured FTP) is a more secured version of FTP that uses SSH (Secure Shell) protocol to encrypt messages between communicating parties. A secure Shell is a protocol that establishes a secure communication session for the delivery of packets over a TCP/IP connection.SSH is the underlying protocol that provides security in SFTP.SFTP is essentially FTP over a SSH, hence provide the same level of security as SSH(Heimstra, 2007). Mailing has also become an indispensable feature of the Internet; through mailing services the Internet provides a stack of protocols at the Application Layer which include POP (Post Office Protocol) to retrieve stored messages from POP Servers. The Post Office Protocol (POP) servers store incoming mails (Bagad & Dhotre, 2003). Simple Mail transfer Protocol (SMTP) servers handle forwarding of mails in a Mail Exchange system. IMAP (Internet Mail Access Protocol) is the newer protocol that provides stability, functionality and security for the retrieval of stored mails. Post Office Protocol, version 3 (POP3) is simple and limited in functionality (Forouzan, 2007).A great many mail agents are available out there, some are freeware, shareware and others are proprietary embedded in applications. In addition to these services, Telnet (Terminal Emulation) is a service that provides remote logons over the Internet to End Systems. It allows a user to connect to a remote host (Gorth & Skandier, 2005). Terminal Network (Telnet) provides remote login capability, which enables a user at a terminal or a personal computer to logon to a remote computer and function as if directly connected to that computer. (Stallings, 2002). The Internet also provides streaming services of audio/video contents which have marked as framework of the Web 2.0. Streaming of stored, live, and interactive media contents have come to fruition with the development of technologies that can implement these services over the Internet. Webcasting, Internet telephony, Internet radios and other services are increasingly being developed. In this chapter, we are going to walk through these enumerated services and others that are being used over the Internet. We shall only discuss client programs (agents) that run these services; the functionality of the server programs is decidedly beyond the scope of this post.
File Transfer Protocol (SFTP, TFTP, SSH)
 File Transfer Protocol
File Transfer Protocol
FTP stands for File Transfer Protocol and allows you to transfer file(s) from one computer to another in a sophisticated manner (CO.LTD, 1997). FTP client programs provide access to files and directories stored of FTP servers on the Internet. FTP is built on client-server architecture and uses a separate control and data connections between the client and the server (Wikipedia, 2014). FTP utilities use clear-text username and password authentication mechanism. FTP stands for the client programs and the protocol that supports file transfer between nodes on a TCP/IP based network. FTP client programs come in Command-Line Interface versions and Graphical User Interface versions. CLI FTP programs were the first to emerge as earlier Operating Systems Text-based Command-Line Interfaces. Virtually, all platforms support the UNIX-Like console FTP utility to manage the operations of file transfer between a client and a server in an IP network. The specifications of FTP were originally stated in RFC (Request Form Comment) 114 on 16 April 1971 by Abhay Bhushan. The specifications of the functionalities of FTP have been revised in a series of RFCs. FTP is supported by both IPv4 and IPv6 networks and is exclusively based on Unicast IPs. In this section, we are going to discuss popular client FTP programs that are available on the Internet some of which are free-of-cost and others are priced.
The most common FTP client software available on the Net are: Filezilla, which is a GUI based program that is used to logon to FTP sites to access directories and files. Files can be in the form of ASCII (American Standard Code for Information Interchange) text-files and/ or binary files. Filezilla is a common client program that can be downloaded from a range of websites freely. Figure 1.0 shows the interface of Filezilla that has established a session between a remote server and a local machine.
Filezilla is a free, cross-platform application that provides File System Manipulation facilities using TCP connect at port 20. Binary files are available for Windows, Linux and Mac OSX. It supports FTP, SFT and FTPS (FTP over SSL/TSL) TCP connections (Wikipedia, 2014).
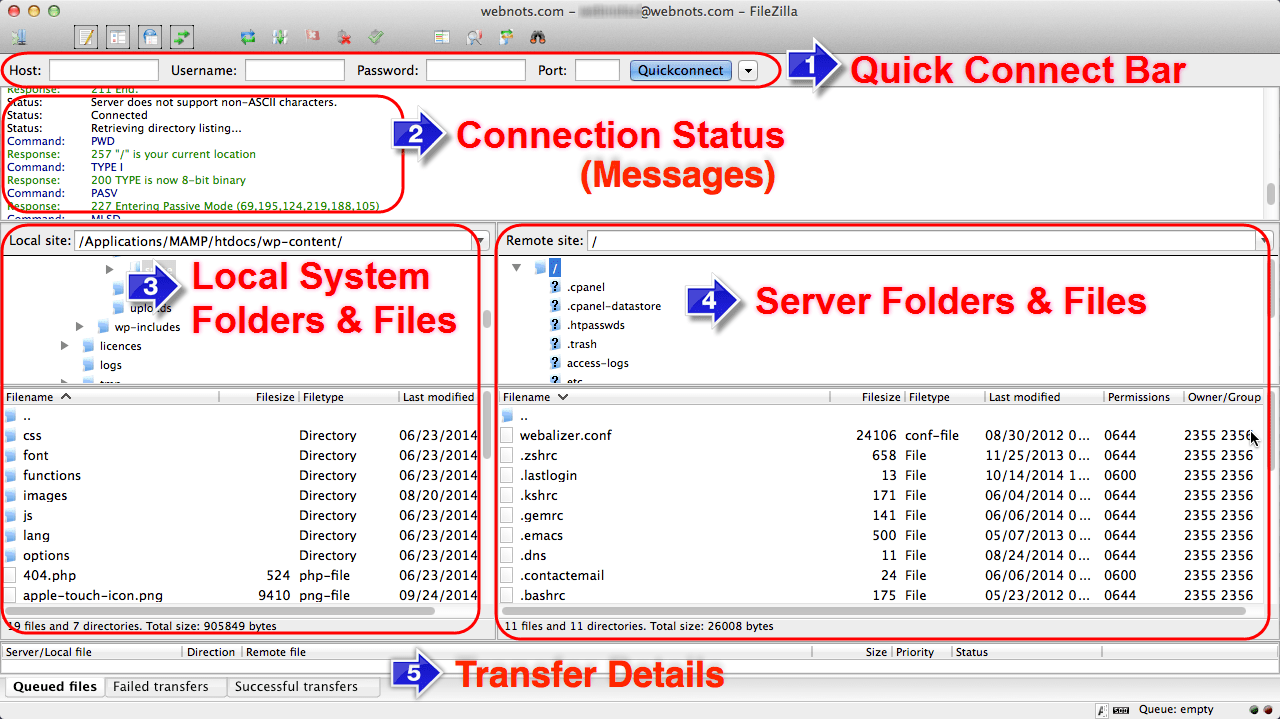 Filezilla client application
Filezilla client application
The features of Filezilla include:
- Transfer of files in FTP, SFTP and encrypted FTPS.
- Support IPv6 addressing scheme on the Internet.
- Multilingual package that is available on over forty languages among which include Arabic, German, French, English, Chinese, Japanese and many more.
- Supports pause and resume of file transfer sessions
- It is a multithreaded application
- It provides bookmarking of favourite site for quick access in the long run.
- It is a highly customizable application that has seed limits set capability.
- Remote file editing
- Provides a persistent connection session.
- Server side searching ability
Downsides of Filezilla are as follows:
- Filezilla stores usernames and password as plain-texts such serve as a potential source for malicious exploit. These files can be accessed by malicious programs to provide headway for intruders to gain access to the user’s account on the server and to damage resources on the system.
Another popular client FTP program is FTP Voyager which also basically provides the integral functionalities of an FTP client program which have been stated earlier. FTP Voyager began as an ActiveX project by Mark Peterson as “FTPFree” (Wikipedia, 2014). FTP Voyager version 16 supportsIPv6, 64-bit and more functionality. Figure 2.0 shows the window of FTP Voyager client package.
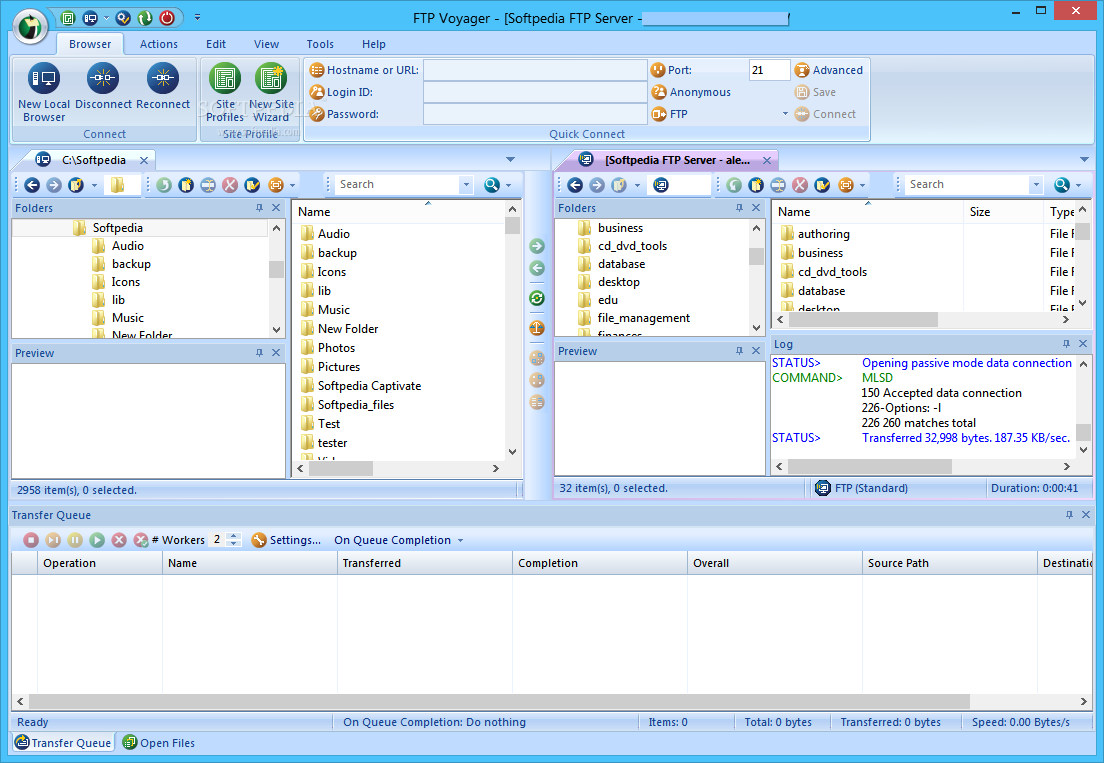 Voyager FTP client application
Voyager FTP client application
Feature of FTP Voyager:
- FTP/FTPS/SFTP protocols
- Directory Synchronization (i.e. synchronization of local and remote directories)
- Multithreading of processes
- Server side file searching and indexing
- Support for proxy server.
- Customizable UI
- Real-time File editing FTP Voyager includes a component called FTP Voyager Scheduler which allows for various actions to be scheduled:
- Uploads
- Downloads
- Synchronizations (Local/Remote)
- File move operation (move up, move down)
- External batch operations
FTP sites can also be accessed at the command-line interface which virtually all platforms support. To access an FTP site at the MS-DOS prompt, you have to first know the FTP URL (e.g., voyager.deanza.tbda.edu) and an account at the site which usually is created by the Administrator of the server. You must also have privileges to the resources on the site; roles and privileges are assigned by Administrators.
To access an FTP site in DOS, follow the following steps:
- Open the Run Prompt and type CMD
- Click Ok which fires up the CMD console.
- At the prompt, type FTP as indicated next.
- To perform the necessary file and directory operations, like get (to download a file from the server), mget to download multiple files which can also be used with a wildcard like *.txt to download multiple files that are text files in the present directory, put is the command to upload a file and as you may guess, mput is the command to upload multiple files which can also use wildcard. Lest we forget, the encoding scheme should be set to ASCII or binary to avoid data corruption.
To perform more operations, type help at the FTP console to see the available commands as shown
- Anonymous login facility is provided by default on most FTP servers which provide access to files and directories available in the public domain. To access these files, a user does not need to have an account or password; instead, the user can use anonymous as the user name and guest as the password (Forouzan, 2007). And in other cases, the username can be anonymous and password is the user’s e-mail address.
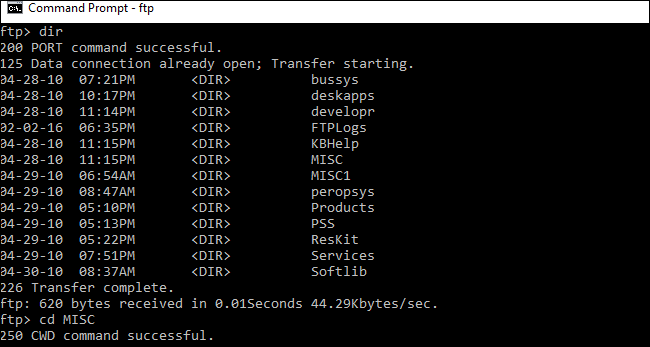
MS DOS FTP client
Birth of the World Wide Web
The web is a pretty recent feature (Electronic mail is an example of an application that pre-dates the Web) of the Internet that has radically changed the way we communicate and perceive information. Researchers at CERN (European Organization for Nuclear Research) were the vanguards for the creation of the World Wide Web — which is a global hypermedia system of information storage and retrieval. The WWW project was originally developed to provide a distributed hypermedia system which could easily access – from any desktop computer – information spread across the world (Gromov, 2012). The web includes standard formats for text, graphics, sound, and video which can be indexed easily and searched by all networked machines. Using NeXT’s object-oriented technology, the first Web server and client machines were built by CERN – the European Laboratory for Particle Physics in November 1990. Since then the Web has truly encompassed the globe and access has proliferated across all computer platforms in both the corporate and home markets. Internet Explorer is also a doorway to FTP sites. It can be used similarly to WWW sites but with small modification by going to View Menu and choosing Open FTP site in Windows Explorer as shown below: In view of the fact that users like GUI based programs, people seldom use DOS based FTP; it is exclusively used by system administrators to transfer huge files in an IP network.
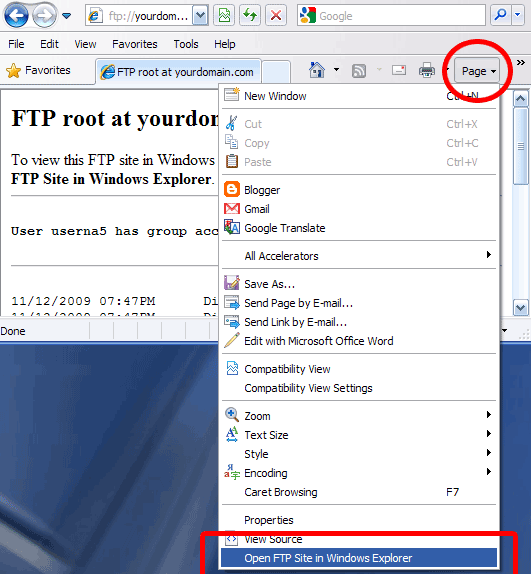
Internet Explorer FTP Access
MAILING SERVICE (SMTP, POPV3, IMAP)
Communication has been part of human civilization; the passing of message from person-to-person and among communities has been a herculean task with the increment of distance. Communication and distance have been inversely related before the advent of the mass media. People used to pass on messages through couriers who will take considerable time to deliver these messages. These messages are also known as snail mails. Postal systems immerged as aid to these bottlenecks by batching mails that belong to the same class for delivery to a particular location. The delivery of these mails took different media (transportation) but the result is work being done and on time. With the advent of the New Media, the face of communication has dramatically changed, which has led to the phenomenon of a global village where messages can be delivered from one point of the globe to another in just a few seconds if not minutes. The New Media has unique advantages that are summarized by Crosbie (2002) as follows: The hallmark characteristics of this New Medium are:
- That individualized messages can simultaneously be delivered to an infinite number of people.
- And that each of the people involved shares reciprocal control over that content. Mailing service is a subset of the vehicles of the New Media; there are plenty of mail servers out there that provide mailing services to clients some of which are costless and others are organization-specific. The way electronic mail works on the Internet is similar to the way the postal system works. E-mail is a blend for Electronic Mail which literally, is an automated version of postal system with the bottlenecks of slow delivery removed and improvement on security and reliability. Email is much older than ARPANet or the Internet (Peter, 2001). At the beginning of the Internet era, the messages sent by electronic mail were short and consisted of text only; they let people exchange quick memos. Today, electronic mail is much more complex. It allows a message to include text, audio, and video. It also allows one message to be sent to one or more recipients (Forouzan, 2007). Early mails were only text-supported; Multi-purpose Internet Mail Extension (MIME) is a supplement that has been developed to support non-ASCII formats in a mailing system. Almost all mail exchangers support MIME that can augment the power of SMTP. Some of these supports are: audio, graphic, video, applications and others. User Agents are client programs in a mailing system that act as the interface with the mail server and the user (or calling program). The following listings are the tasks of a User Agent:
- Composition of new messages
- Reading of messages
- Reply to messages
- Forwarding messages
- Handling of mailbox
These tasks and other accessories are provided by user Agents on behalf of the user or calling program.
- Command-Driven
- Graphical User Interface (which are event driven) Command-Driven Agents were the earliest and are now obsolete. But they are still found in server environments where they are used by Administrators. They are apparently text-based console applications. For example, a user can type the character r, at the command prompt, to reply to the sender of the message, or type the character R to reply to the sender and all recipients. Some examples of command-driven user agents are mail, pine, and elm. GUI-based Mail Agents are relatively modern and are event driven (e.g., UIs with icons to respond handle user events like click, keystrokes and others). They are pretty popular among consumers in the market. Some examples of GUI-based user agents are Eudora, Outlook, and Netscape (Forouzan, 2007). Notwithstanding, there are provisions for web-based access to emails in the form of HTML. Web-based access to mailboxes is becoming a commonplace for most users. The idea is somewhat simple; a user makes a request to a mail server through a HTTP request and the server in turn replies with a form which contains space for user_id (i.e., email address) and password. These credentials are matched with the stored authentication file to provide access to the user’s account in the form of plain an HTML page format. The forwarding of a message is fundamentally done by SMTP server.
Introduction to mailing with Outlook Express:
Microsoft Outlook Express is a product-line User Agent that Provides access to ones mail account. Outlook comes as part of the Office Suite. It is quite a robust Agent that provides access to POP, SMTP, IMAP servers. The figure below depicts the window of a mail being composed in Outlook including an attachment. As we mention earlier, web-based access is also possible a browser. The following screenshot show an account creation form for Hotmail.
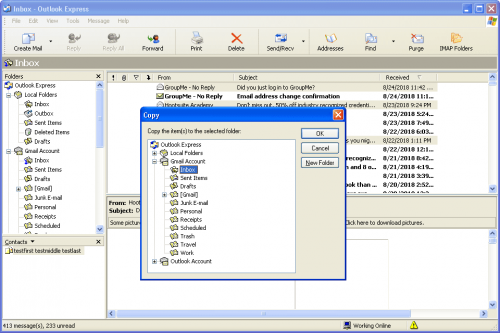
Microsoft Outlook Express
In this form the user is required to provide the necessary information to have an account with Hotmail, which is just one of the mail service providers out there. Others include Gmail, Yahoo and private organizations. The syntax of an email is as follows
| Username | @mail_server_name | .domain |
|---|---|---|
| The username can be any valid unique identifier for that user e.g., Fatmata | @ is just a directive that signal a computer name is next e.g., @yahoo, @universityofmakeni e.t.c. | The period precedes the domain, the Internet nodes are identified by a hierarchical namespacing with dot (.) at the root domain followed by Top Level Domains (TLDs). These TLD are virtually three-character identifies like .edu, .mil, .org, .com, .net and emerging domains like .biz, .info. IANA (Internet Assigned Numbers Authority) is responsible for these names and numbers in the Internet. |
An example of a valid e-mail address can be somebody@xyz.com. The first portion of this address identifies the user, the @xyz is the mail server name and the .com is the domain of the address which is a company/commercial domain. Domain names are labels that have been mapped to their respective IP addresses in a system called DSN. The principal catalyst behind the scene is a Domain Name Server that resolves name labels to IP addressed and vice versa.
Telnet/SSL

Telnet Server
Telnet (Terminal Network) is a terminal access mechanism that was developed in the early days of mainframes that used the Unix OS which provides access to resources. Telnet is the name of the client program and the protocol as well. As other popular programs, there are CLI versions of Telnet and GUI packages some of which are shipped with Popular Operating Systems like Windows, Linux Mac OSX, and Solaris among others. To use Telnet in windows you must turn it on in programs applet in Control Panel. The screenshot below shows a GUI-based application called Tera Term which is available free on the net. Telnet connects at TCP port 23. With Telnet, a user can configure devices in a network, use remote programs and access data. Hey! Telnet is insecure! There is no encryption of user data is a Telnet session. An eavesdropper can use packet analyzers, packet sniffers or other toolkits to intercept data including username and password which are all in plain-text. Because of this creepy flaw, SSH (Secure Shell) is preferred to Telnet to establish a more secured session. SSL (Secure Socket Layer) is just an encryption service that is provided at the transport layer to protect the transmission of data. Socket can be viewed as a gateway to an application in the ISO-OSI and Internet models. It is a combination of an IP and port numbers, that a node on the Internet and a particular process to communicate with. I conceptual view of a socket is shown below: Windows version of Telnet is shown in the diagram below
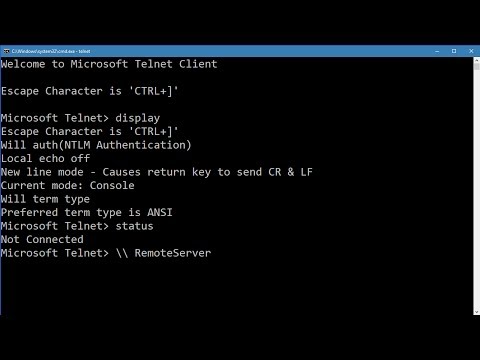
Telnet Client on MS DOS
Audio/Video Streaming (Real-Time Streaming Protocol)
Streaming of voice (or video) data from the Internet is increasingly becoming a popular means of passing messages. A few decades ago, broadcast radio and TV (either cable or satellite) were the only ways of conveying audio and video data between parties. The Internet was used only for text and images. Research is being done to exploit the Internet for the delivery of audio and video contents. Streaming means a user can listen to (or watch) the file after the down-loading has started(Forouzan, 2007).The Internet is overly becoming a principal channel for audio and video streaming. The contents delivered over the Internet can be classed into three categories:
- Streaming of stored media contents (i.e., Audio/Video)
- Streaming of Live media contents (i.e., Audio/Video)
- Streaming of Interactive media contents (i.e., Audio/Video)
- Streaming Of Stored Media Contents (i.e., Audio/Video)
- Streaming of stored files on servers is also known as on-demand delivery of contents. These files are compressed so that they can utilize low bandwidth networks. Examples of stored audio files are songs, symphonies, books on tape, and famous lectures. Examples of stored video files are movies, TV shows, and music video clips (Forouzan, 2007).
Streaming Of Live Media Contents (I.E., Audio/Video)
Classic applications of live streaming are Internet Radio which broadcast data through the Internet and Internet TV that uses the Internet to deliver data. Some Radios have Internet versions as well as Conventional broadcast mechanism (s).
Streaming Of Interactive Media Contents (I.E., Audio/Video)
The two stated streaming procedures above are passive and unidirectional. This third category is interactive and bidirectional if not Omni-directional. Classic applications of interactive streaming are Internet Telephony and Internet teleconferencing. The nitty-gritty of these streaming procedures is beyond the scope of this book. Inclined readers can read texts on Data Communication and Networking. Voice Over IP is an interactive service the Internet provides’ instead of using the conventional circuit switched network for telephony, Voice services are provided in a packet switched network. Voice data transfer with other capabilities is provided in a packet switched IP network. This reduces the overhead for corporations that are separated geographically separated by not having to link their networks with multiple carriers to provide telephony service. Two protocols have been designed to handle this type of communication: SIP and H.323 (Forouzan, 2007). Session Initiation Protocol (SIP) serves as a dialog controller to initiate, manage, and terminate data transmission sessions (calls). H.323 is a standard designed by lTV (Internet TV) to allow telephones on the public telephone network to talk to computers (called terminals in H.323) connected to the Internet. There are quite a considerable number of programs available on the Net for voice and video communication over the Internet. Some of these are Skype TM, Viber, WhatsApp and many more. These packages provide less costly service over the Internet compared to GSM, GPRS, and other carriers.
The Web (HTTP, HTTPS, S-HTTP)
The World Wide Web is a product of an extensive research activity at CERN (Centre European pour la Recherché Nucleaire) that was later changed to European Laboratory for Particle Physics by Tim Berners-Lee and other pioneers in Switzerland. The web is a global information storage and retrieval system that provides an array of information and resources. It is thought to be the most colossal library in the world. The web is just one of the applications of the Internet that is based on the Hyper Text Transfer Protocol. The WWW is based on two tier (client-server architecture) distributed system, in which the client (browser) initiates a request to the server at port 80 using a TCP transport service. So the WWW is newer than the Internet. The concept of the WWW was created at the end of the 1980s when the Internet was already well established.
Characteristics of the WWW
The web has grown into the most immense product of human endeavor. The ubiquity of the web has given it some striking characteristics that are summarized by (Raychaudhury & Pal, 2001).
- Platform Independence: The material can be consulted with any type of computer and with any browser.
- Time Independence: The material can be accessed at any time
- Multimedia Capability: Can show moving images, animation, etc.
- Editing: Easy to update the contents.
- Sharing: Users can share single copy.
- Space Saving: Takes less storage space
- Delivery: May be shipped over networks.
- User Interface: Not standardized The diagram below shows the relationship between the WWW and the Internet (which is the underlying infrastructure). The WWW is a collection of sites (locations) where web documents (i.e., web pages) are stored. These sites are interlinked by Hyperlinks (links on a texts/images/sounds or icons that can take you to another location within a single page or another page within the same site; it can also be an inter-site link).Hypertext is an intuitive way to navigate web pages.
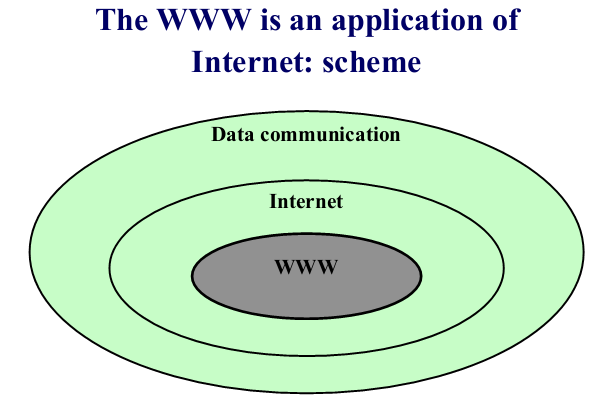
Relationship between the Internet and the World Wide Web
Uniform Resource Locator HTTP provides a unique addressing scheme to locate resources on the web. Web resources have addresses that are used to access documents on the web. Addressing is not a new phenomenon; it has played a vital role in the evolution of the Internet. The syntax and semantic of a VALID URL is shown below: protocol://hostname:port/../resource_path e.g., http://www.unimak.edu.sl
Working With Browsers (Client Programs)
In the distributed world-wide information system; web servers can be primarily accessed with client programs called browsers or web browsers. In the early days of the web, Mosaic was the first client program that was developed in 1993 by NCSA (National Commission for Supercomputer Applications) in the US. Other browsers that appeared in the market are listed below in their respective orders of appearance:
- Chrome
- Netscape
- Microsoft Internet Explorer
- Opera
- Mozilla Firefox
- …
Other browser like Safari, and UC browser are also available out there. However, 90% of the Internet population uses one of the two most popular browsers Netscape Navigator or Microsoft Internet Explorer (Massally, 2008). The web with all these potentials can be a daunting place to access relevant materials. This is simply because the Web has not centralized authority; access to information on the web can be a marathon task. This has led to the creation of search engine and directories.
What is a Search Engine?
A search engine a program that transverses the web pages to match with keyword entered by clients in it. The search results are returned in a ranked pattern with the most useful results at the top and the less relevant searches below. These search engines have robots and crawlers that transverse the web to index web pages for easy retrieval of search queries. The most common search engines are: Google, WebCrawler, Bing, AltaVista, Info seek, Excite, Search NZ and many more. These tools have fundamentally the same functionality though they have superficial differences. To understand the querying pattern of a particular search engine, you may have to read the help page(s) of that search engine. This is very crucial when one wants to get a quick response for a search query.

Popular Search Engines
What is a Directory/Subject Tree?
A directory is essentially a pseudo-classification of sites and/ or web pages that can be accessed base on their respective classes. Directories are also known subject trees. A subject tree is a broad list of categories that branch off into subcategories, such as that found in Yahoo or Te Puna. These are not organised by librarians so the subject classification does not conform to any established system (Massally, 2008). Jargons of the Web: the jargons are the language that is spoken on the web. These include blends, reformations and other techniques. They are thus:
Homepage: this can be a starting point of a website in using the Web. It is the first page that is opened when your browser fires up to access a web site! A homepage can also be a personally authored web page that contains information about the owner.
Hypertext: a text that contains a pointer to another location within a page or out of it. A hypertext is seen as an anchor to another location. This is an example of a hypertext to the website of Unimak.
Hyperlink/Hot link/Link: this is a link/pointer to a location in the WWW distributed system. Hyperlinks are the support behind the success of the Web since one can navigate fluidly in it. This can also serve as a source of embarrassment for user because they can get lost easily in the surfing process.
Broken Links: Non-existing links that are dangling in the web with their locations removed or dysfunctional.
Web server/Webserver: a server program that ‘supplies’ web pages to clients (browsers) on request. These programs support concurrent request because they are multithreaded application programs.
Newbie: a person that is new to the Internet and/ or one of its services (e.g., e-mail, mailing list, newsgroup, web, Telnet, ftp e.tc.).
Cookies: A string of characters that holds some information about the client and must be returned to the server untouched (Forouzan, 2007). Websites use cookies to offer a personalized experience to users and to gather information about website use. Many websites also use cookies to store information that provides a consistent experience between sections of the site, such as a shopping cart or customized pages.
FAQ: Means Frequently Asked Questions; these are recursive questions asked by Newbies in newsgroups and discussion forums. FAQs have become de facto way of listing and answering probable questions that may be posed by visitors to a site or service.
Remote: A system which one can connect to through a network. A remote resource one that is not available on one’s computer, it may be a file on a distant node over the Internet.
Local: available on one’s machine or system. Local resources can be found on one’s hard drive or storage media.
Shareware: a piece of software that is available free initially on trial basis.
Freeware: a program that is freely available for download. Freeware is mostly attributed with Open Source Movement (Creative Commons Attribution).
Download: to download is to get a copy of a file from a remote system (in our case a web server) to one’s own hard drive. The screenshots below depict the process of download.
Upload: to upload is to send data to a remote system. It is the reverse of download; images, documents, sound and video files can be uploaded to other systems.
The Internet is so complex that resources can be daunting to locate; the independence of Autonomous Systems makes it hard to centrally control the Internet. Different organizations, corporations, governmental agencies, research institutes and businesses control “patches” of the Internet. These organizations have different access policies to their resources. There have been well-known documented error messages that blowup on the Net. These messages are informative and provide clues to solving access problems. The table below lists the error messages and their causes that show up in client programs in the Internet.
Popular Error Codes
| Status Code | Label | Description |
|---|---|---|
| 400 | Bad Requst | There is a syntac error in the request |
| 401 | Unauthorized | The request lacks proper authorization |
| 403 | Forbidden | Service is denied |
| 404 | Not found | The resouce is not found |
| 405 | Method not allowed | The method is not supported in this URL |
| 406 | Not acceptable | The format requested is not acceptable |
Other common services on the Internet are:
Mailing list (Listserv): this is a discussion forum where similar interest groups converge to share thoughts through the normal mailing system. Members signup for the service through their e-mail addresses to which messages are sent directly. Discussion forums are available for all walks of live. Computer Science students for example, can form a forum where threads of conversations are forwarded to members of the group.
One has to be thoughtful not to fall short of the netetiquettes (net etiquettes) when posting on a discussion forum to avoid flaming. Some posts (mostly by neophytes) can unwittingly lead to flaming wars, which can resort to verbal or textual abuses in the forum among discussants. Flaming war is literally Argumentum Ad Hominem, where participants post heinous comments about others that could possible “let them go ballistic!” Newsgroup (Usenet): This is another discussion platform where like-minded folks meet to discuss topics of interest.There are over 18,000 different ‘newsgroups’ where people discuss everything imaginable (Massally, 2008). Usenet is also known as Internet news. Usenets have URLs that is akin to other services on the Net. The addressing pattern is an inverted tree that provides a hierarchical name system for Usenet servers. Clients have to have newsreader programs to read posts in Usenet. Note: Not all ISPs support newsgroups.
Conclusion
In this chapter, we have tried hard to abstract the rigors of the Internet by defining concepts in the simplest possible form to get the point right. We shed light on the most popular services of the Internet. We also markedly showed the difference(s) between the Internet (which is the underlying architecture/infrastructure) and the WWW (a service provided on top of the Internet). We discussed services like Telnet (Terminal Network), FTP, Multimedia streaming, SSH/SSL/TSL and other protocols. These services are suited for different demands, e.g. the use of FTP to transfer massive files and documents in a research setting, the use of the web to access documents and e-mail for messaging. Some applications were decidedly not covered in this book (e.g., Gopher and DNS), they can be known by incline reader in books on Data Communication and Networking (e.g., Data & Computer Communications by William Stallings).
Useful links
Free Book Spot —– E-books Directory
Book Yards Wiki-books Bookboon TutorialsPoint
Sierra Leone News Sites
Awoko News Awareness Times Politico News News Watch Salone Standard Times Cocorioko News
Foreign News Sites
New York Times Aljazeera BBC Reuters News Time Africa
Government Sites (SL)
Anticorruption Commission SL Bank of SL National Ebola Task Force NEC SL
Online Dictionaries and language corpora
Macmillan Online Dictionary Oxford Online Cambridge Online Merrian-Webster Dictionary.net Reference Encyclopedia InfoPlease Britannica Abbreviations Acronym Search All Acronyms Acronym Finder Wikipedia
Search Engines
Bing Duck Duck Go Ask.com Dog Pile Yippy Google
Web Portals
MSN Yahoo All the Web Education Portal
References
Bagad, V. S., & Dhotre, I. A. (2003). Computer Networks (1 ed.). Shaniwan Peth, India. CO.LTD, S. C. (1997, March 3). E-mail: connecting people across the Globe. United States: SULTAN CHAND & CO. LTD. Crosbie, V. (2002). What is the New Media. Forouzan, B. A. (2007). data Communication and Networking. New York: Mc-Graw Hill. Gorth, D., & Skandier, T. (2005). Network Study Guide (2 ed.). San Francisco, United States: Sybex. Heimstra, J. (2007). CompTIA Network+. Massally, A. (2008). Introduction to the Internet. Peter, I. (2001). History of Email. Retrieved August 12, 2014, from nethistory.info Raychaudhury, A., & Pal, J. K. (2001, December 4). Internet Services for Exploring Social Science Resources. Calcutta, India. Stallings, W. (2002). Data & Computer Communications (6 ed.). New Delhi, India: Prentice-Hall. Wikipedia. (2014, June 13). Trival File Transfer Protocol. (Wikipedia) Retrieved August 10, 2014, from Wikipedia:

Leave a Comment